
Student MFA
Helping to prevent unauthorised access to UCD student accounts
Multi-Factor Authentication for UCD Student Accounts
UCD IT Services is introducing Multi-Factor Authentication (MFA) for all student accounts, as an important IT security measure.
MFA adds a second layer of security to help prevent unauthorised access to your sensitive information online. Essentially, students will be required to enter a code as an additional security step when logging into their UCD Connect accounts.
No action is needed for now, and UCD IT Services will be in touch directly with all students in the coming months about the next steps.
Why do we need MFA?
Your password alone is not enough to keep identity thieves from getting into your account.
You could be at risk of having your password stolen if you:
- Click the links in email messages
- Download software online
- Use the same password for multiple accounts
If an identity thief steals your UCD username and password, they can:
- Delete your contacts and files
- Lurk in your email account to get information about your work
- Use your account to get to your personal accounts (bank, credit card, etc.)
- Impersonate you to gain access to your contacts’ accounts
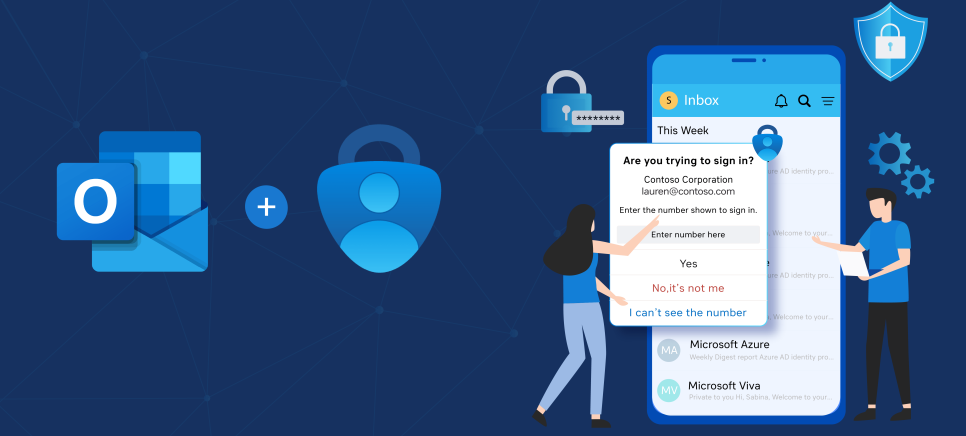
Microsoft Authenticator App
UCD IT Services recommends the Microsoft Authenticator App for students
Push Notifications
- Quick and Easy Login: When signing in, you’ll receive a push notification on your mobile device.
- You simply enter the number shown on the login screen into the app and approve the sign-in.
Works Anywhere
- Push notifications work over Wi-Fi or mobile data.
- If you're offline, you can use time-based one-time passcodes (TOTP) generated by the app.
- These codes refresh every 30 seconds and don’t require network access.
About the Microsoft Authenticator App
UCD IT Services recommends using the Microsoft Authenticator App for students as your second-factor authentication method. The app is available to download from the app store on your device.
- The Microsoft Authenticator App does not track your geographic location information or device usage.
- Camera access is only required during initial setup to scan a QR code.
- Data usage to receive a 'Push Verification' is less than 2kb per Push.
- Push Verification works via Wi-Fi or mobile networks.
Please Note:
Installing the Microsoft Authenticator App does not mean you have to share your mobile number. You can register your smartphone as a tablet, and you will not be required to share your mobile number.
There are also additional options available outside of the app such as receiving an SMS or a voice call to confirm your sign in if you do not use a smartphone. To configure one of these methods you can select the I want to set up a different method option that is available when stepping through the Microsoft Authentication set up as shown in the video above.
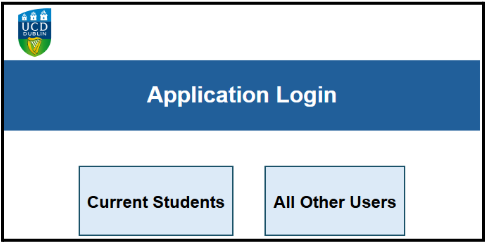
New Step in Log-in process
To facilitate the introduction of MFA, a new step will be added for all staff and students when logging into UCD IT Systems to ask users to indicate if they are a current student or not. When accessing systems, users will see a splash screen with two buttons as shown to the right:
- For Current Students
Once Current Students is selected from the screen shown, students will log in using their @ucdconnect.ie email address rather than their UCD Connect Username. After entering the email address and clicking Next, there will be a second prompt for the password to be entered.
- For All Others Users (including Alumni and Applicants)
Once All Other Users is selected from the screen shown, all other users will proceed to the username and password screen where you log in using your username and, if required, receive your regular Duo MFA notification as per the current process.
Further details on the new log in process are available on our Knowledge article (opens in a new window)here.

.jpg)